As cloud-native applications become increasingly prevalent, Azure customers are entering a realm where applications can be easily purchased and deployed within their subscriptions with just a few clicks. However, a challenge arises when it comes to updating or upgrading these Azure resources to newer versions. One approach is to containerize and abstract them from Azure resources, but this can lead to the loss of crucial integrations. What if there was a method for publishers to maintain some degree of control over the resources they deploy into your subscription with a simple click-and-collect process?
Enter Azure Managed Applications. An Azure Marketplace offering that facilitates ongoing collaboration between publishers and customers, extending beyond the initial installation phase. It fosters a relationship between partners and customers that is not only safer and more auditable but also more streamlined than traditional B2B supply chain interactions.
This blog post delves into the appearance of this Azure Marketplace offering and the dynamics between the publisher and the customer. Additionally, we'll investigate how it enables publishers to enhance infrastructure provision and deliver continuous support, all while providing customers with simplified management and configuration options.
Resource Allocation
So, you find a fancy Azure Marketplace offering and you want to install it but it's a Managed Application offer. What does this mean for the resources you deploy?
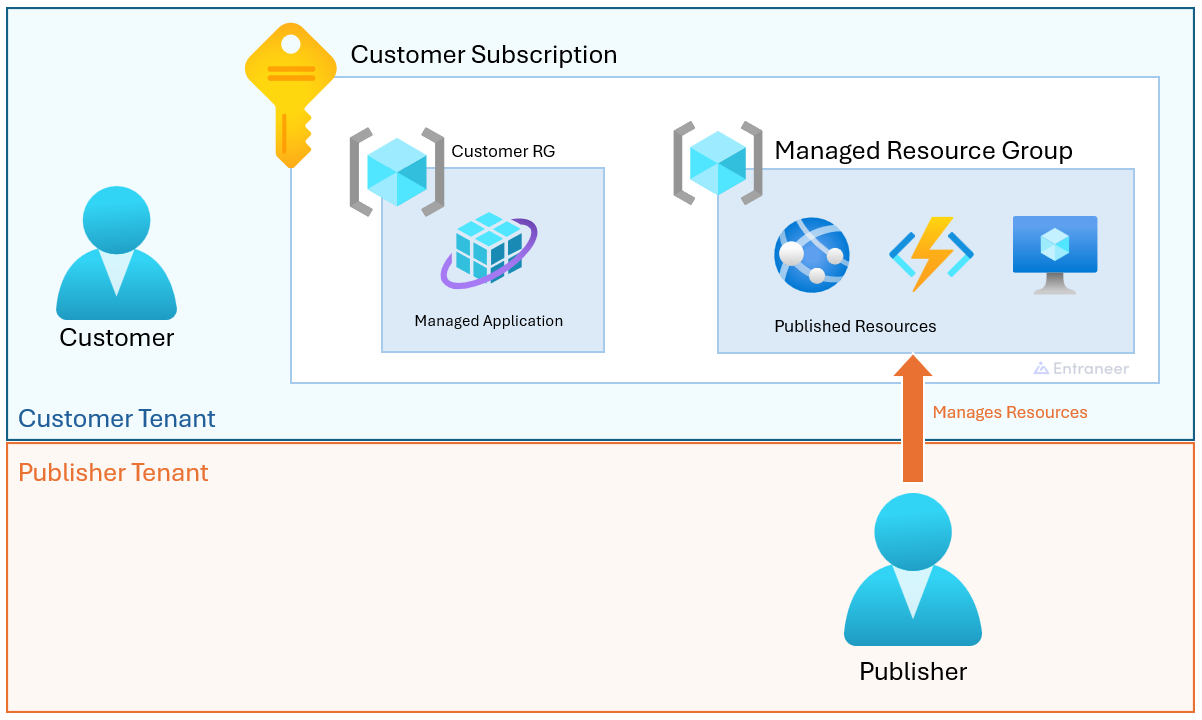
Well, let's start from the point of view of the customer. After you install this offering you will notice that you will have two main resources:
- Managed Application
- Managed Application Resource Group
Inside the Managed Application Resource Group, you will find all the resources you expect to run the service. That's not very unusual. It's not until you try to edit one of these resources will you notice that you are not permitted to edit all your new resources. You may own these resources but you likely don't have the permissions to manage them 1.
Swapping to the perspective of publishers, they will be notified of your purchase and automagically have your managed resource group appear in their Azure Portal. They can read and write all the resources deployed in your newly managed resource group (which sits in your subscription).
In essence, a Managed Application creates shared resources owned (and billed) by the customer. Both parties have full visibilities of these resources but write permissions are configured by the publisher.
It's important to acknowledge that each Managed Application is different, while many will be managed by the publisher, the customer might be responsible for maintaining and configuring the infrastructure.
Managed Application Resource Group
The managed Resource Group operates similarly to any other resource group, serving as a container for resources owned by the managed application. Access to this resource group might be restricted for the customer, as they typically do not manage the individual resources unless permission settings are altered. The publisher has the option to forego access to the managed resource group. Generally, all resources are deployed during the initial marketplace deployment, allowing visibility into the anticipated billing cycle.
Managed Application Resource
The Managed Application Resource serves as a management hub for the offering, offering tailored metrics, configurations, and contact details, and serving as the primary avenue for deleting a Managed Application. Upon deployment, customers can customize the security, permission and limited amount of properties. This resource's location in the subscript can be customized during deployment.
Integration into client resources
Permissions
by default, the publisher can always be an active contributor or owner of the client's managed resource group. This grants them authority to manage resources, update configurations, and perform maintenance tasks. Conversely, customers are granted read permissions for all resources, except certain ones like App Service Configuration. The publisher can grant specific permissions to customers for integration or customization during installation. For instance, Apporetum enables clients to manage network integrations, DNS settings, proxies, and blob storage configurations to tailor the installation to their needs.
Additionally, the publisher can allow specific data actions such as viewing key vault secrets and reading SQL servers. It's important to recognize that these permission settings can be modified at any time and are not apparent until the marketplace offering is installed.
Deployment Capabilities
What happens when we want to integrate a Managed Application's resources with a customer's existing resources? Either the customer can be given the permissions to create connections, e.g. VNet peering, or the customer integrates these resources from the deployment stage. Azure provides a set of custom UI components for the deployment to integrate with customer's existing storage, VNet and key vaults. This allows the publisher to integrate these without needing permission for these resources all while allowing the customer full control over the resources.
When integrating with customer-owned resources, the publisher faces certain limitations. For instance, the customer might offer an existing virtual network but require private DNS Zone integration and subnet integrations for the App services. These tasks are currently not feasible and would necessitate post-deployment actions on the part of the customer.
When to use Managed Applications
Customers should consider using Azure Managed Applications when they require data sovereignty for their resources or data. This is particularly important for organizations that need to adhere to specific regulatory requirements regarding the location and handling of their data. Additionally, Azure Managed Applications are ideal for customers who need to integrate Azure resources within their existing network boundary, such as connecting cloud services to on-premises infrastructure. This allows for a seamless extension of their IT environment into the cloud while maintaining control over their network topology. By leveraging Managed Applications, customers can benefit from a robust ecosystem that offers turnkey solutions through the Azure Marketplace or Service Catalog, simplifying deployment, enhancing security, and streamlining management, which is essential for Managed Service Providers (MSPs), Independent Software Vendors (ISVs), and corporate central IT teams.
Security
Managed applications provide unmatched flexibility and security controls for supply-chain managed resources. However, you have to be very careful how it is configured at the time it is published. You should be implementing JIT (if the customer has a P2 License). You can read how to "recover" from deploying with JIT without a P2 License.
Just-In-Time Access for the publisher
Azure Managed Application Just-In-Time (JIT) is a pivotal security feature designed to provide publishers with temporary elevated access to a managed application’s resources. This access is confined within a predetermined time frame, ensuring that while publishers have perpetual read-only access, JIT access grants them enhanced privileges necessary for specific operations such as troubleshooting and maintenance.
The process for enabling JIT access is straightforward. Publishers list their managed applications on Azure Marketplace with an indication that JIT access is an option. Consumers, at the time of deployment, have the choice to activate JIT access for their particular managed application instance. Post-deployment, they retain the ability to modify JIT settings as needed. When a publisher requires access for maintenance or troubleshooting, they submit an access request. Upon receiving this request, the consumer has the authority to grant the requested elevated access for a designated duration.
This JIT access mechanism affords consumers a heightened level of governance over their managed resources. They possess the discretion to either grant or reject access requests, aligning with their operational requirements. This approach not only empowers consumers but also safeguards against the risks associated with unwarranted or enduring access by publishers, thereby bolstering the security posture of the managed resources.
Customer considerations
Customers must grasp the concept of Managed Applications thoroughly. In the absence of Just-In-Time (JIT) access, there’s a slim chance that external entities in the supply chain could gain access to resources. These resources might contain sensitive network and business information.
However, when properly set up with JIT, these types of resources establish an advanced and sophisticated security measure. This configuration allows customers to enjoy the advantages of having their resources managed by publishers, while also retaining a degree of flexibility in their operations.
Management
Publishers are given the ability to manage deployments via the Azure Managed Application Centre and the Azure Managed Application Service Catalog. This gives publishers access to navigate to the appropriate subscription and managed resource group.
Wrapping Up
Hopefully, you’ve understood the benefits of Azure Managed Applications for both you and your clients, as well as the potential pitfalls. It is my hope that this article has been a valuable resource on your journey with Managed Applications. Should you require support in deploying your Managed Application, feel free to reach out to us, and we’ll arrange a discussion. Our team possesses extensive experience in setting up and launching applications such as Apporetum on the Azure Marketplace, where we’ve witnessed its successful growth.
Footnotes
-
Not all Managed Application Resources have deny assignments to edit ↩