Azure Managed Applications are a useful tool for both publisher and customers to share the responsibilities of an application in the customer's azure environment. They have some extensive features but some obvious security holes which can be mitigated through the use of "Just-In-Time Access".
What is JIT for Azure Managed Application
Azure Managed Application Just-In-Time (JIT) is a crucial security feature designed to grant publishers temporary elevated access to a managed application's resources. This access is confined within a predetermined time frame. While publishers maintain perpetual read-only access, JIT access provides them with enhanced privileges necessary for specific operations, such as troubleshooting and maintenance.
With JIT, customers can control when publishers have access to the resources of an Azure Managed Application. They have two options:
- Auto-Approval Mode: In this mode, JIT requests are automatically approved. This approach is ideal for audits.
- Manual Approval Process: In this mode, JIT requests require manual approval by a customer admin. This adds an extra layer of security.
How to request access when JIT is enabled
Here's how the process works for both the publisher and customer to allow for access:
- The publisher navigates to the Azure Managed Application.
- They request contributor or owner permissions for the application.
- If approval is required (in the manual approval process), a customer admin reviews the request.
- Once approved, the publisher account gains contributor access for just enough time to perform maintenance tasks.
Customer's Licensing Requirements
Securing your Azure Managed Applications against supply chain risks is crucial. When accounts with access to your resources are beyond your control, the risk becomes significant. To mitigate this, it’s essential to thoroughly vet your providers and establish a high level of trust.
For instance, the Apporetum team employs a dedicated publishing tenant with robust security measures to prevent supply chain attacks. However, Microsoft offers JIT to allow you to control when publishers have access to your Azure Managed Application’s resources.
JIT access is not free for all organizations. A P2 license is required to enable JIT within your tenant. You can even accidentally enable JIT without the necessary license. Once enabled, there’s no turning back 1.
How to Fix a JIT Deployment Without Sufficient License
Let's say that your customer has enabled JIT without understanding that they need a P2 License to use it. The first symptom will be visible when you go and try to request access to their resources. You run the request and get a successful notification. All is good then?
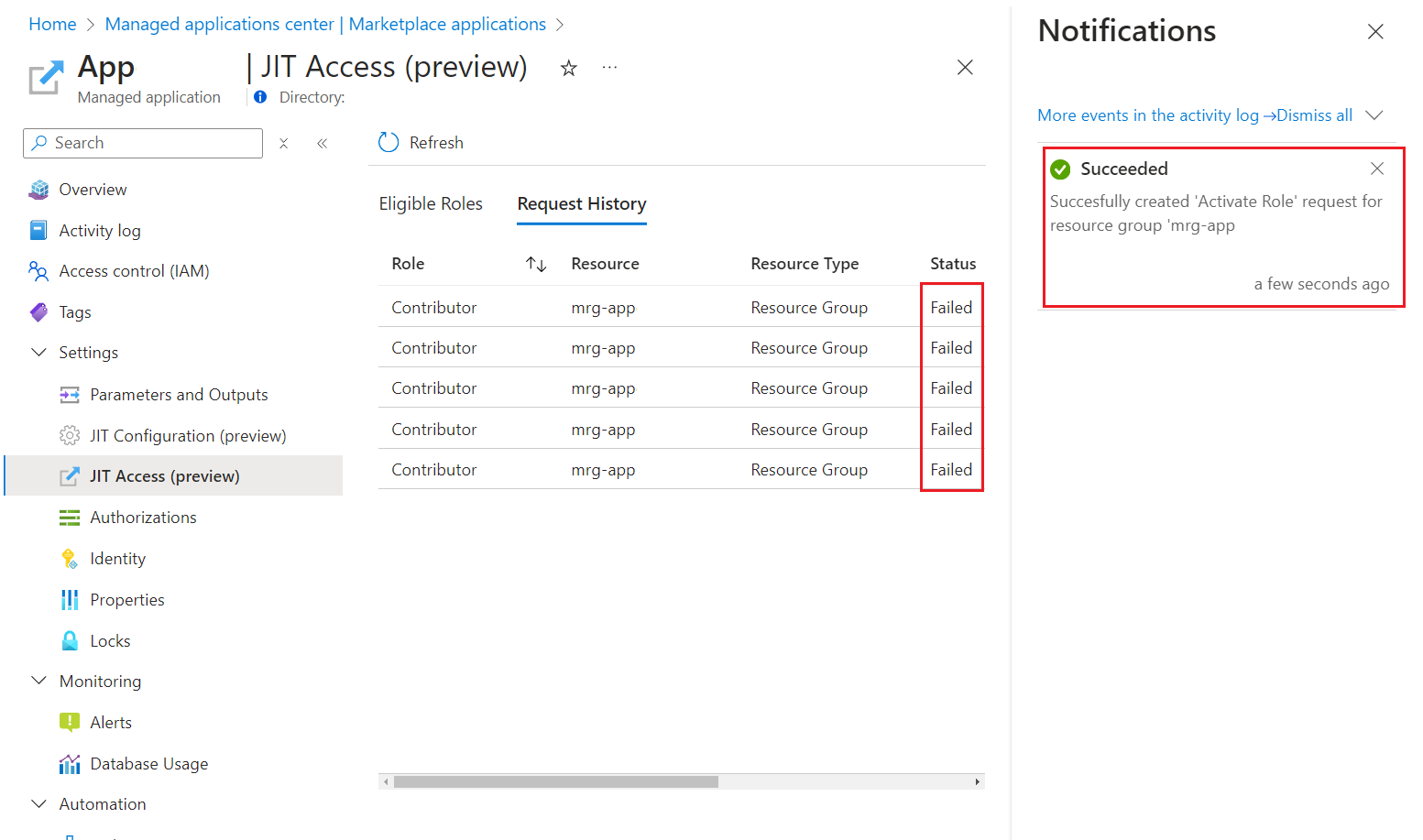
Nope, if you dig deeper into the request history you will see that your request got denied for apparently no reason at all...
Plain and simple. You won't be able to fix this unless you talk to Microsoft Support. Even then, I have had no success.
I know that's not what you want to hear if you are here but let me discuss some ways you can mitigate this problem. All the following solutions do not give your publishing accounts more access. If they did it would make JIT a pointless security control. However, they should give your customer the ability to move forward with the deployment.
Microsoft Product Team. If you read this. Can you make it so that customers can turn off JIT after the deployment 🙂.
Your Options
Here are the options which I have discovered by being put in a place where the customer does not want to redeploy.
1. Update JIT settings Via API
Let us start with the best option which might not always be possible. Get your customer to run some commands to disable their JIT access policy. You will notice that this can't be done via UI and has to be done via Azure Management APIs. First you will need to get your deployment's ID for the Managed Application. That is where you can actually request the JIT so I assume you know where it is. Under properties, you will find the ID property or fill in the blanks of the following command if you are not bothered.
az login
# Update JIT Access
az rest --verbose --method PATCH \
--uri '/subscriptions/{subscriptionId}/resourceGroups/{resourceGroupName}/providers/Microsoft.Solutions/applications/{applicationName}?api-version=2019-07-01'
--body "{\"properties\": {\"jitAccessPolicy\": {\"jitAccessEnabled\": false }}}"
# OR with the Managed App Id
az rest --method PATCH --uri '{managedAppId}?api-version=2019-07-01' --verbose
--body "{\"properties\": {\"jitAccessPolicy\": {\"jitAccessEnabled\": false }}}"
Jit Access should be disabled if the customer has enough permission (e.g. they were the user who published it).
You can see the progress of this command (as it async) by following this blog which describes how to retrive async progress in azure.
2. Step Up Customer License
Technically, all your customer needs is a single P2 license to enable JIT. Maybe that's all you need to deploy your application and get it up and running. In practice this is harder in an organisation than it sounds on paper. However, I believe it is worth mentioning.
3. Update Customer Permissions for an Azure Managed Application
Here is the backup option you should take if the customer is being difficult. This is quite involved but will allow you to give your customer all the permissions they need to access their resources. E.g. remove all the block permissions on their accounts. In essence what we will do is deploy a new version of the application from the Azure Marketplace with adjusted permissions. Then we will get them to run a command which with update their permissions on their deployment. Then as a clean up task we can republish the app with the permissions removed.
I wrote a blog on exactly this, refresh customer permissions which is a valid way to fix this issues if you are happy with giving your customer extra permissions.
Wrapping Up
You have seen why you and your customer should enable JIT, but you have also seen how it can go wrong. Hopefully this article helps you in your Managed Application Journey. As always if you need assistance in deploying your Managed Application you can reach out to us and we will set up a time to chat. Our team has experiance in configuring and deploying applications like Apporetum to the Azure Marketplace and have seen it flourish on the Azure Marketplace.